Permissions may include:
Login IDs
Unless otherwise communicated, your Windows account is synchronized to the Barracuda Email Protection Portal. You will not need to create an account, but in some cases, you may be prompted to verify your Microsoft 365 Credentials.
Message Log
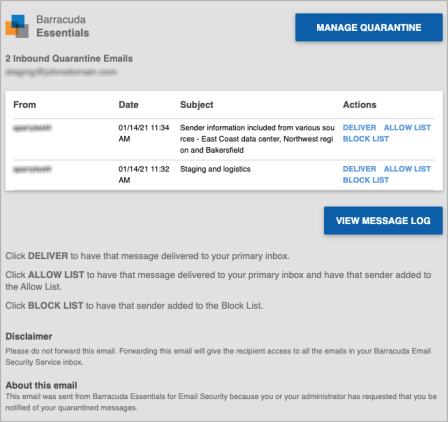
The Barracuda Email Security Service web interface includes the Message Log, which you can use to manage your quarantined messages.
Quarantined Mail
When enabled, you are notified regularly when you have quarantined messages. Your Waypoint administrator sets the default quarantine notification interval, or if you have permission, you can set the interval on the Settings > Quarantine Notification page.
Please Note that quarantined messages are deleted after 30 days. For more information, see Quarantine Notifications.
The links in the Actions column allow the user to:
- Deliver – Click to deliver the message to your regular inbox.
- Allow List – Click to allow the sender. All future messages from the sender are allowed and go directly to the user's regular inbox.
- Block List – Click to have the sender added to the block list.
Figure 1. Sample Quarantined Email Notification
Manage Mail
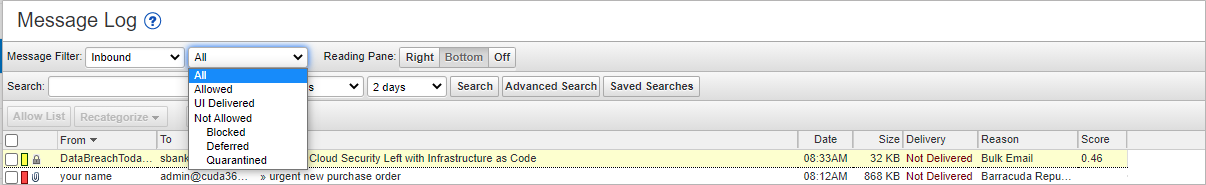
Use the Message Log to manage mail. The Message Log page displays all email messages from the Barracuda Email Security Service to your account. You can filter messages by All, Allowed, UI Delivered, Not Allowed, Blocked, Deferred, or Quarantined using the drop-down menu. Note that messages are deleted after 30 days.
Figure 2. Filter Messages in the Message Log
Messages are blocked due to the following:
- Spam and virus policies set by your administrator for the domain and
- Your administrator sets email address or domain block policies and emails from other users for the domain.
Messages are deferred for various reasons. Click the Help icon on the Message Log page for more information and details on searching for and filtering messages.
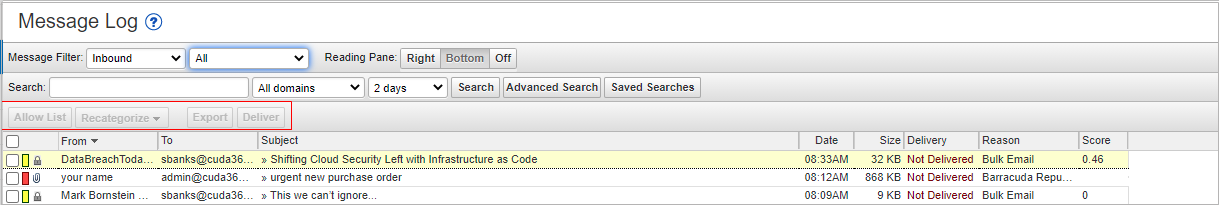
Select one or more messages from the Message Log page, then click on an action. To select all messages, select the check box at the top of the Message List.
Depending on the message filter, once you select one or more messages, you can take the following actions:
- Allow List – Senders of selected messages are added to the allow List; note that you cannot add blocked messages to the allow List.
- Recategorize – You can change the category when one or more categorized emails are selected. For example, if the message is categorized as Corporate but should be categorized as Marketing Materials, you can change the category via the Recategorize drop-down. This action submits this email message for recategorization to your selected category. If you select Other and enter a custom category, the category updates for that particular email message. For more information, see Email Categorization below.
- Export – Selected messages are exported to a CSV file. When prompted, enter a file name and select whether to save to your local desktop or network.
- Deliver – The service attempts to deliver the selected messages to your mailbox; note that you cannot deliver messages blocked for Advanced Threat Protection (ATP). If a message is successfully delivered, the Delivery Status changes to Delivered. The mail remains in the log until you select the message and click Delete. A notice will be displayed in your browser window if the mail cannot be delivered, and the Delivery Status will not change. If messages are not delivered to the recipient's mailbox, it may be due to a filter on the mail server or a service on your network catching the mail as spam. Check with your system administrator for more information. Additionally, check your local trash/spam folder for the mail.
Figure 3. Message Actions
Email Categorization
If the Reason for a message in your Message Log displays as Email Categorization, the email from this sender is categorized as not necessarily spam but something that you may have subscribed to at one time but no longer want to receive—for example, newsletters and memberships, or marketing information. Email Categorization assigns some of these emails to specific categories, which the administrator can decide to allow, Block, or quarantine. Supported categories display in the Message Log Reason field as:
- Email Categorization (corporate) – Emails sent by a user at an authenticated organization from an MS Exchange Server that involves general corporate communications. Does not include marketing newsletters.
- Email Categorization (transactional) – Emails related to order confirmations, bills, invoices, bank statements, delivery/shipping notices, and service-related surveys.
- Email Categorization (marketing) – Promotional emails from companies such as Constant Contact.
- Email Categorization (mailing lists) – Emails from mailing lists, newsgroups, and other subscription-based services such as Google and Yahoo! Groups.
- Email Categorization (social media) – Notifications and other emails from social media sites like Facebook and LinkedIn.
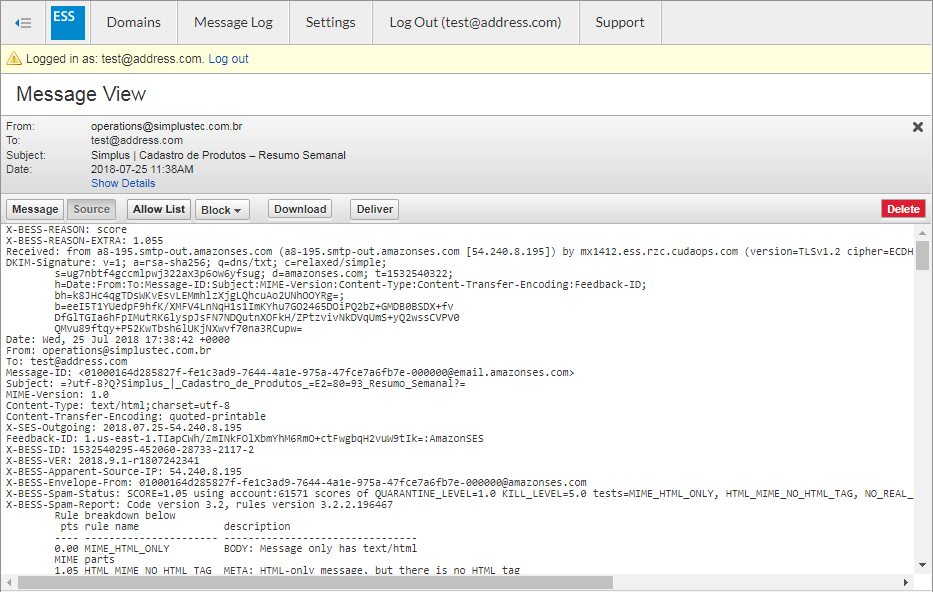
View Message
To view the message source, headers, and available options, double-click the message; the message content will be displayed. You can take the following actions:
- Click Source to view all headers
- Click Allow List to allow the sender
- Click Block and select whether to block the message Domain or Email
- Click Download to download the message to your local system or network
- Click Deliver to deliver the message to your regular mailbox
- Click Delete to remove the message. (This option is available for quarantined messages only.)
- Click Report as Incorrectly Blocked for a message that should have been delivered to your regular mailbox. This includes messages that are not spam. (This option is available for quarantined and blocked messages only.)
- Click Report as Incorrectly Delivered for a message that should have been blocked. This includes spam messages.
Alternatively, you can use the Settings > Sender Policy page to exempt or block senders. See Set Exempt and Block List Policies later in this article for additional information.
Figure 4. Message Source with Headers
Set Quarantine Notification Interval
Quarantined messages are deleted after 30 days.
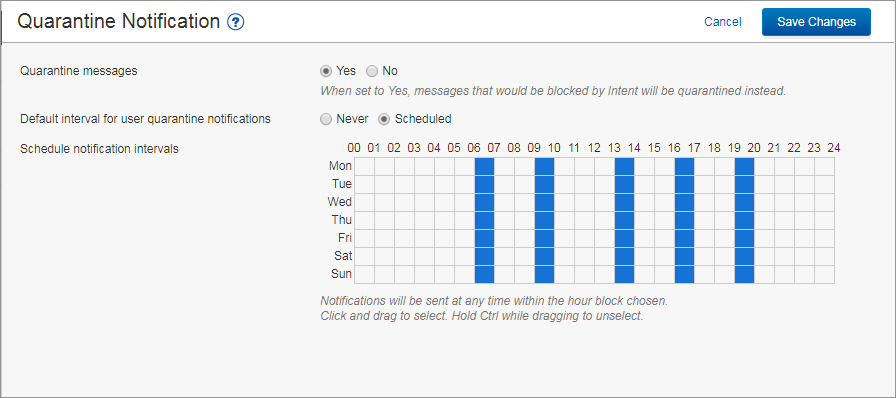
You can direct the Email Security Service to notify you by email when you have quarantined messages. When set to Yes, messages that would usually be blocked are instead quarantined. This setting does not apply to messages blocked by Sender or Content policies. On the Settings > Quarantine Notification page, select Scheduled. Click and drag in the Schedule notification intervals section to set the day and time for quarantine notification email delivery. Click to clear a selection. Alternatively, select Never if you do not want to receive quarantine notifications. Click Save Changes to save your settings.
Figure 5. Set Quarantine Notification Interval
Set Exempt and Block List Policies
Use the Sender Policy page to specify whether to block, allow, or quarantine messages from a specific sender or domain. These are called exempt/block list policies. To create a new policy:
- Go to Settings > Sender Policy page, and enter the email address or domain in the Sender field.
- Select whether to Block, Exempt, or Quarantine the sender from the Policy drop-down menu.
- Optionally, you can add a comment to indicate why you created the policy.
- Click Add to save the policy:
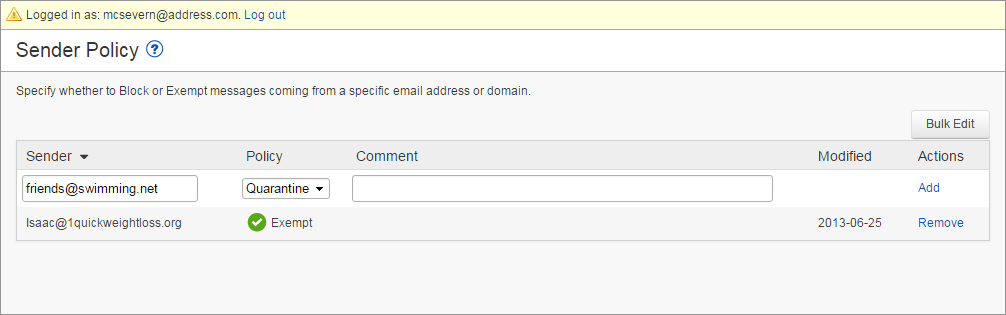
- To remove a policy, click Remove in the Actions column for the sender policy you want to remove.
ink Quarantine Accounts
You can add additional email addresses in the same domain for which the quarantined email will be forwarded to this account. From the Settings> Linked Accounts page, enter the email address in the Account field, select whether to Link the account without verification and click Add.